Quick Specs
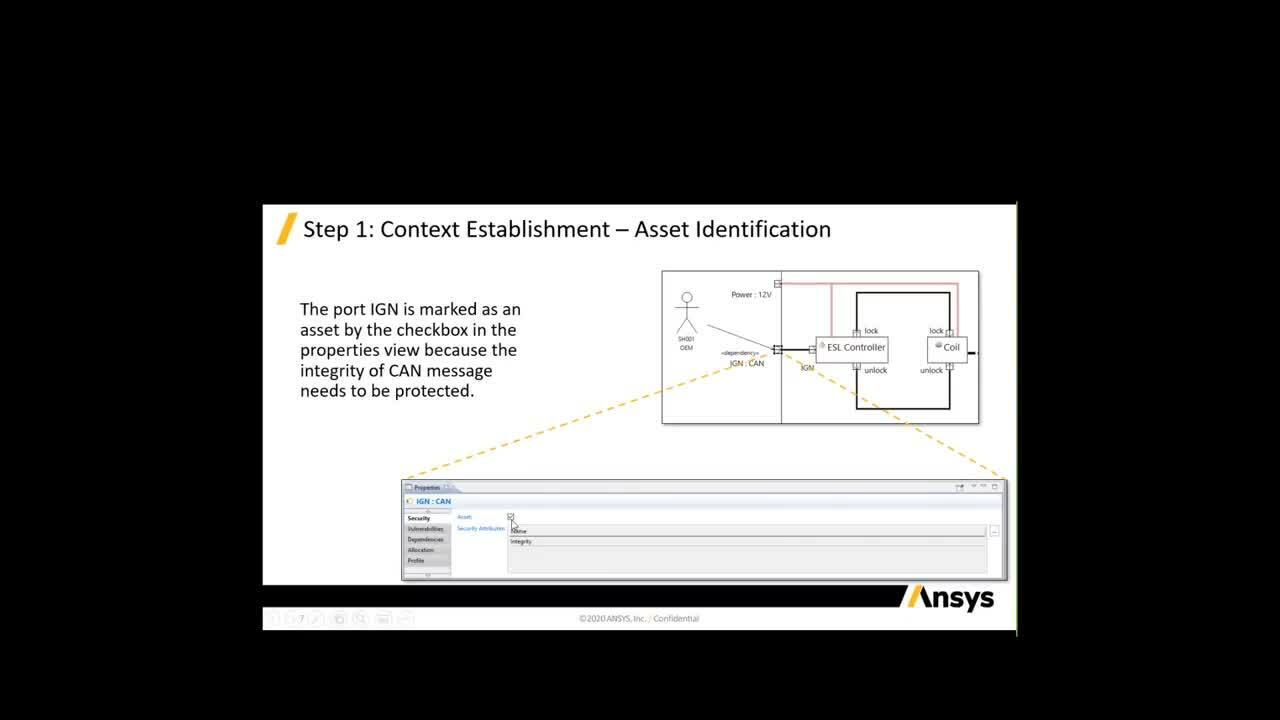
Across the entire electronics architecture, Ansys medini analyze for Cybersecurity carries out a system-oriented cybersecurity analysis strategy to quickly identify vulnerabilities and design weaknesses, and address them to mitigate any real-world threats.