-
-
Access Free Student Software
Ansys empowers the next generation of engineers
Students get free access to world-class simulation software.
-
Connect with Ansys Now!
Design your future
Connect with Ansys to explore how simulation can power your next breakthrough.
Countries & Regions
Free Trials
Products & Services
Learn
About
Back
Products & Services
Back
Learn
Ansys empowers the next generation of engineers
Students get free access to world-class simulation software.
Back
About
Design your future
Connect with Ansys to explore how simulation can power your next breakthrough.
Free Trials
ANSYS BLOG
May 5, 2023
Where Safety and Cybersecurity Intersect in Connected Vehicle Tech
Analyzing risk and exposing vulnerabilities in one convenient requirements-based workflow
As the demand for self-driving connected technology grows, so do conversations around vehicle safety and cybersecurity. Many advanced driver assistance systems (ADAS) in today’s vehicles are already operating autonomously using a combination of sensor, camera, radar, and other technologies to course-correct driver error or detect and avoid nearby obstacles. But just like any other connected tech, autonomous vehicles (AV) are vulnerable to cyberattacks.
Ever-increasing vehicle connectivity increases the number of system surface attacks via flashed firmware, Bluetooth, Wi-Fi, cellular, and GPS, for instance — through which an attacker can trigger a fault in steering, braking, powertrain, or other systems. A successful attack can ultimately lead to compromised safety, from downed systems to the loss of data and privacy.
For original equipment manufacturers (OEMs), such events can also lead to financial loss and tarnish brand recognition. It’s a big reason why ISO (the International Organization for Standardization), requirements address this level of safety and cybersecurity — and Ansys software is ready to help OEMs meet them.
“In the past, OEMs were driven by known vulnerabilities that were typically uncovered by hacker groups,” says Mario Winkler, lead project manager of physics at Ansys. “This reactive approach required them to go back to their implementations or products already on the market to catch up, which in the end is very costly. Ansys medini analyze and Ansys SCADE Suite offer a proactive, seamless solution that is requirements based. Combining both tool sets enables manufacturers to identify and patch any system vulnerabilities in the early stages of development.”
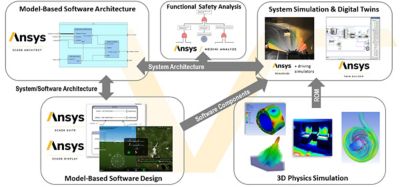
Cracking the Secret Code with SCADE
Like other cyber-physical systems, connected vehicle systems are a permanent and growing target for malicious attacks. The average vehicle relies on complex code defined by hundreds of embedded control systems (ECUs) in communication with an in-vehicle network (IVN) — pathways that give hackers and other malicious actors an opening to find and exploit software vulnerabilities. Adopting secure coding enables manufacturers to remove any vulnerabilities and stop cyberattacks before they happen.
SCADE is a modeling tool that can deliver safe and secure auto-generated code to address any issues on the software side in step with the SEI CERT C coding standard, which provides rules for secure coding in the C programming language. The goal of these rules and recommendations is to develop safe, reliable, and secure systems by eliminating undefined actions that can lead to undefined program behaviors and exploitable vulnerabilities.
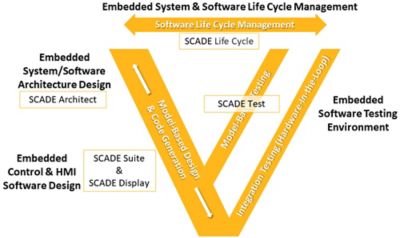
Fast, Accurate Systems-based Analysis for ISO Compliance
ISO covers automotive safety and automotive cybersecurity in two separate requirements. As it applies to our discussion of SCADE, Safety deals with the prevention of harm the system can cause to its environment and is covered by ISO 26262-1, “Absence of reasonable risk.” There’s also ISO/SAE 21434, “Road vehicles — cybersecurity engineering,” which is the automotive industry-based cybersecurity standard.
With these requirements in mind, running a cybersecurity analysis within medini analyze can help identify assets and their security attributes, then systematically identify system vulnerabilities that can be exploited as points of attack. From there, the software can estimate the potential for an attack, associate risk with each threat, then plan and execute appropriate security measures based on previously identified risk.
Using medini analyze, OEMs can obtain some estimation of how likely certain attack paths really are, right down to the effort it takes to execute them. This includes identifying the risks and possible consequences to determine how critical the need is, as well as what measures need to be taken to reduce these risks.
“Ansys medini is all about threat analysis and risk assessment based on discovery,” says Winkler. “The software gives OEMs more context. Specifically, who are the key stakeholders involved, and what kind of interest do they have in these assets? And if these assets become compromised, what is the impact if an attacker takes over, and where do these interactions lead?”
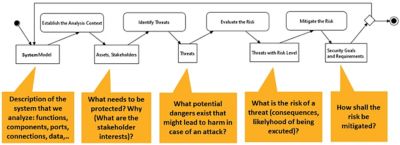
Going with the medini analyze + SCADE Workflow
To ensure safer, more secure connected vehicles systems requires the introduction of certain mechanisms (controls) to mitigate risk — requirements that will later apply to software modules and components. Establishing a continuous workflow between both medini analyze and SCADE enables the sharing of architecture, system design, and models that support safer, more secure designs.
“When you come to the end of production or a specific phase in your product design, combining both SCADE and medini analyze enables you to avoid all of the safety issues associated with connected vehicle tech according to ISO standards,” says Francois Xavier Dormoy, senior product marketing manager of physics at Ansys. “So, it’s this combination that provides a fully integrated, complete solution. Both tools take on the heavy lift for OEMs to navigate a certification process mired in rules-based standards, overcoming system complexity with certainty.”
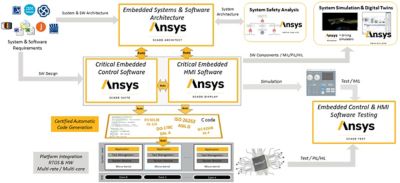
How It Works
To give some additional perspective, at the beginning of a workflow involving both products, medini analyze evaluates risk levels and comes up with a mitigation strategy to reduce them. This strategy is then formed or expressed in requirements that need to be fulfilled by the system later — for instance, to identify the need for an encryption here, or an authentication there.
This activity involves requirements that need to be implemented or secure communications that need to be established and encrypted, along with the appropriate system software to be in place to do this kind of encryption in a secure way. The sharing of system designs from medini analyze to SCADE helps accomplish these goals to ultimately capture an overall design that is more detailed, formalized, and modeled, from the system software to the individual hardware components.
Both tools also include interfaces to requirements management systems that enable a very smooth, straightforward requirements flow. If the user needs additional software requirements to be secure or needs to enable security controls in a certain way, these activities can be directly addressed in SCADE with secure code generation.
Thankfully, at least for the moment, there are relatively few hacking incidents involving passenger vehicles. However, as OEMs ramp up to full autonomy, cybersecurity risks will continue to grow as reliance on vehicle applications, connectivity, and the increasingly complex, integrated electronics supporting higher AV function grows. SCADE and medini analyze will continue to grow right along with these systems, in step with ever-changing automotive system requirements.
Learn more about how Ansys medini analyze and Ansys SCADE can support you in your automotive safety and cybersecurity objectives, and take both for a test drive by signing up for a free trial.